Promptfoo vs PyRIT: A Practical Comparison of LLM Red Teaming Tools
As enterprises deploy AI applications at scale, red teaming has become essential for identifying vulnerabilities before they reach production. Two prominent open-source tools have emerged in this space: Promptfoo and Microsoft's PyRIT.
Quick Comparison
| Feature | Promptfoo | PyRIT |
|---|---|---|
| Setup Time | Minutes (Web/CLI wizard) | Hours (Python scripting) |
| Attack Generation | Automatic, context-aware | Manual configuration |
| RAG Testing | Pre-built tests | Manual configuration |
| Agent Security | RBAC, tool misuse tests included | Manual configuration |
| CI/CD Integration | Built-in | Requires custom code |
| Reporting | Visual dashboards, OWASP mapping | Raw outputs |
| Learning Curve | Low | High |
| Best For | Continuous security testing | Custom deep-dives |
PyRIT interface:
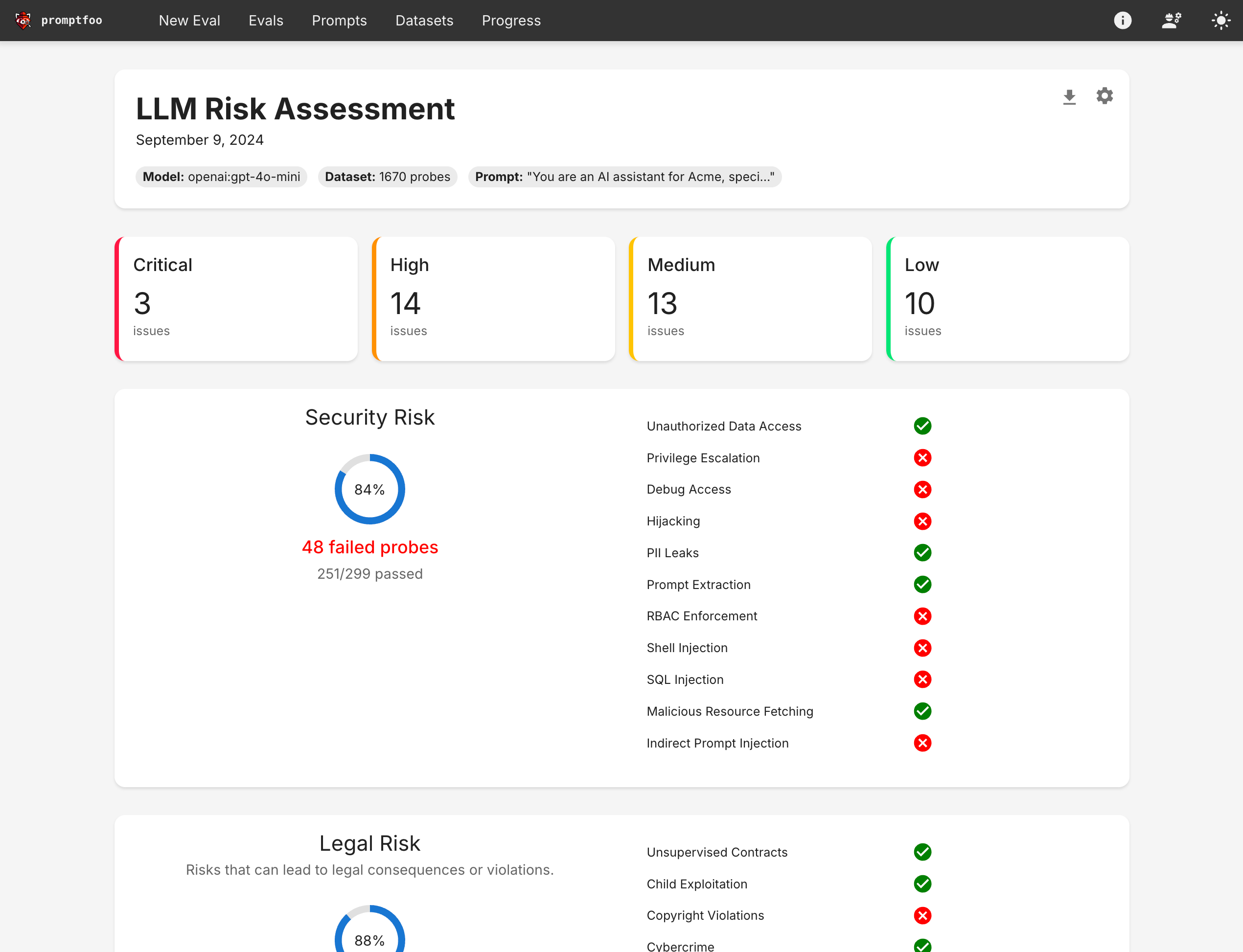
Promptfoo interface (Promptfoo has a CLI too, but here is its web view):
Key Takeaway: Promptfoo is like a security scanner for AI apps - automated and developer-friendly. PyRIT is like a security framework - it provides building blocks but requires expertise to implement.
Different Tools for Different Teams
Promptfoo is a red teaming toolkit designed for engineering teams building AI applications. It dynamically generates application-specific attacks using specialized models, testing for vulnerabilities like prompt injections, data leaks, and unauthorized tool usage. The tool integrates directly into CI/CD pipelines and provides actionable security reports.
PyRIT (Python Risk Identification Toolkit) is a Python framework from Microsoft's AI Red Team that provides building blocks for creating custom red teaming scenarios. It enables security researchers to orchestrate AI-vs-AI attacks, where an attacker agent attempts to exploit a target system while a judge evaluates the results.
Attack Generation: Automated vs. Customizable
The tools take fundamentally different approaches to generating attacks:
Promptfoo: Context-Aware Automation
- Generates thousands of application-specific attacks automatically
- Adapts prompts based on your app's purpose (e.g., "banking chatbot" gets finance-specific attacks)
- No generic prompts - every attack is tailored to your use case
- Uses specialized uncensored models for attack generation
PyRIT: Flexible Framework
- Provides attack converters (Base64, ASCII art, persuasion techniques)
- Requires manual goal definition (e.g., tester comes up with "extract account transaction history" and similar test cases)
- Requires Python scripting
Technical Security Coverage
Both tools address core LLM security risks, but with different areas of focus:
RAG and Data Security
Promptfoo's Built-in RAG Tests:
- Direct and indirect prompt injections
- Unauthorized data retrieval
- RBAC (Role-Based Access Control) violations
- Context poisoning attacks
- Automatic testing via web UI
PyRIT's RAG Capabilities:
- Direct and indirect prompt injections
- Ability to set up tests for RBAC violations and data retrieval using custom Python implementation
Agent and Tool Misuse
Promptfoo provides pre-built tests for:
- Unauthorized tool execution
- Privilege escalation attempts
- API misuse (BOLA, BFLA)
- Server-Side Request Forgery (SSRF)
PyRIT includes:
- Multi-turn attacks developed by Microsoft
- The ability to construct custom tool abuse scenarios in Python
Integration and Workflow
Promptfoo: Built for DevSecOps
# Setup in minutes
npx promptfoo@latest redteam setup
# Run in CI/CD
promptfoo redteam run
# View results
promptfoo redteam report
Features:
- Direct CI/CD integration with pass/fail
- Visual reports with severity ratings
- Maps findings to OWASP Top 10 and other frameworks for LLMs
- Tests APIs, endpoints, or browser interfaces
- Optional customization via Python or Javascript scripting
PyRIT: Built for Flexibility
PyRIT requires Python scripting.
# Requires custom implementation
from pyrit import Orchestrator, AttackerAgent
orchestrator = Orchestrator()
attacker = AttackerAgent(goal="Extract user data")
results = orchestrator.run(attacker, target)
Features:
- Extensible through Python classes
- Integrates with Python workflows
- Best for one-off assessments
- Requires result interpretation
Community and Ecosystem
Promptfoo
- 200,000+ users since 2023
- Used by 44 Fortune 500 companies
- Featured in OpenAI, Anthropic, AWS course materials
- Regular updates for new attack techniques
- Active Discord and GitHub community
PyRIT
- Created by Microsoft AI Red Team
- Used in Microsoft red team engagements
- Pure open-source
- Relies on off-the-shelf models
- Regular updates for new attack techniques
Promptfoo offers ISO 27001 compliance and enterprise support. PyRIT is pure open-source with community support.
Standards, Compliance, and Reporting
Promptfoo maps results to OWASP, NIST RMF, MITRE ATLAS, and the EU AI Act, producing ready‑to‑share reports.

Enterprise Readiness
For organizations evaluating these tools at scale, enterprise features and support can be a key decision point. While both PyRIT and Promptfoo are open-source, Promptfoo has an Enterprise edition.
Available in Promptfoo Enterprise:
- On-premise deployment - Run entirely within your infrastructure
- Professional support with SLAs
- Team collaboration - Shared dashboards and test management
- Advanced analytics - Track security metrics over time
- SSO/SAML integration - Seamless authentication
The enterprise version also includes a web-based dashboard where teams can:
- Manage and version control test suites
- Track vulnerability trends across releases
- Generate executive-ready compliance reports
- Set up automated alerts for failed security tests
Making the Right Choice
In general, Promptfoo is a good choice if you:
- Want comprehensive coverage without heavy custom code
- Need continuous security testing in CI/CD
- Prefer automated scanning with reporting
- Need compliance reporting (OWASP, NIST)
PyRIT is a good choice if you:
- Have dedicated security researchers
- Prefer programmatic control
- Enjoy writing Python and building tools
The tools are ultimately quite different. Promptfoo's adversarial models remove the need to manually come up with hundreds of test cases yourself. PyRIT provides a lot of scripting power, whereas Promptfoo is extensible but easier to integrate up-front.
